In our continuing scam report series, where we test competing spy phone software to see if they can really do all that is advertised on their website, we have decided to turn our focus to Webwatcher for Android.
Webwatcher is one of the oldest spy phone software companies and software. This review will focus on the Android version to determine if it really is a scam, that is, you get nothing for what you pay for, or, if it genuinely is a working product, even with a few flaws.
Read on for more information.
This report will be split in to the following sections:
Investigating the software claims
Seeing if what they advertise on their website is really what the software can do.
Investigating the software website
Looking at the website and seeing if there are any discrepancies in terms of accuracy of information or if this is one of several sites as part of a scam ring.
Investigating the company
Seeing if this company is well-known for producing many scams of this nature.
Investigating the software you receive after purchase
Looking in to whether or not the scam software actually works and, if it does, if it delivers on any of the features or claims outlined in the first section of this report.
Investigating where the scam originated from
Collating all our evidence and cross-referencing it with any other scam software information we have to find the true provider of this scam.
Protecting yourself from scams like this
Explaining how you can use real software such as FlexiSPY if you wish to monitor a device instead of and saving money on your FlexiSPY purchase in the process.
Investigating the software claims
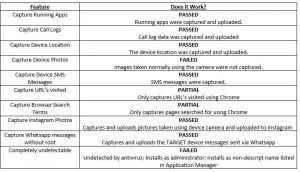
According to the Webwatcher website their Android software has the following features. For those who don’t want to read the entire document you can see below whether or not the advertised features worked or not.
Looking at the results below, whilst Webwatcher does deliver on the majority of what the website offers there are a few features that simply do not work as advertised or only work under certain conditions. For example, URL capturing using just the Chrome browser is something that many customers may not accept because not everyone uses the Chrome browser on an Android device. Others simply choose to use the default Browser application and, if they do, they will not get this Webwatcher feature.
Furthermore, Webwatcher heavily advertises that the software is completely undetectable once installed. This is just not true, as we discovered during our testing. There are a few ways you can easily spot that Webwatcher has been installed and then proceed to remove it.
Investigating the software website
The Webwatcher website does not look like a scam website at first glance. In fact, it looks more reputable than other spy phone software vendors.

However, when you look specifically at the Android section things do get interesting.
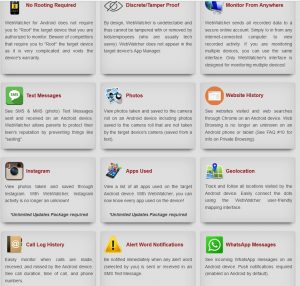
You can see from the above feature list that there are not that many features that you get for your money. This makes Webwatcher less feature rich than the likes of FlexiSPY or Mspy. Furthermore, some of the features advertised are quite misleading.
For example, you only get Whatsapp messages captured if you purchase an optional Webwatcher component according to the website above but, inside the Webwatcher portal, this does not seem to match the information you are given there, as we will show you later.
Investigating the software received after purchase
After you purchase Webwatcher you have two ways to install the software on to a compatible Android device. You can follow the steps given in the email you receive or you can get installation instructions from inside the online portal.
Using the online portal to install can be quite complex. There is no installation wizard and the option to install and the directions are tucked away inside the Settings menu under an option called Downloads. Here you can see all your existing licenses, whether or not they are activated and view the steps to install them.
During our testing we ending up contacting Webwatcher support several times for when we wanted to reinstall the software. There is no apparent way for a user to easily reinstall the software themselves using the same license code without getting help from Webwatcher support too who will then deactivate the license for you, ready for you to reinstall again.
This is not ideal. For one, many people may be under a time deadline and do not have time to contact support to get their license deactivated and second, there is no need to really involve support in this process. Companies such as Mspy and FlexiSPY allow customers to reinstall the software without customer support intervention so, having to get Webwatcher support to help each time can be somewhat time consuming.
Needless to say, after you purchase the software you get full instruction for how to install the software.
Installing Webwatcher
Webwatcher advertises itself as not requiring root and, in certain ways, this makes the software so much easier to install, but, this also offers limited features and an easy way to remove the software, if you know where to look.
Installing Webwatcer actually can take some time, even though rooting is not required. This is due to how the Webwatcher installation method is designed. It has five parts, which are all explained below.
Part 1 – Install a pre-installer (called ATI Client)
Upon downloading WebWatcher it installs a pre-installer that then downloads the main application when opened. You have to log in to your WebWatcher online portal from inside this application to start the download process.
Part 2- Download the main application
Once the main application is downloaded it is then installed.
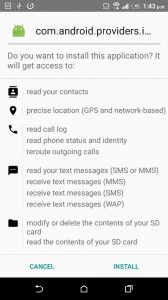
The application is installed as com.android.providers.internal.security and is visible in Application Manager.
Part 3 – Set application permissions
After this application has been installed you must grant it usage permissions so that it can start monitoring.
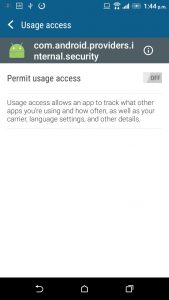
The application also has to be granted accessibility permissions.
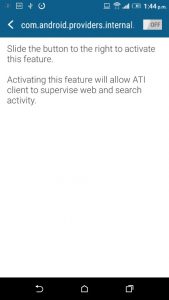
Part 4 – Install application as an Administrator
The software then installs itself as an Administrator to stop it from being easily removed from Application Manager.
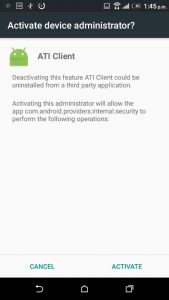
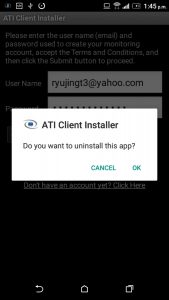
Part 5 – Remove the original preinstaller
Once the main application is installed the preinstaller (ATI Client) is then removed.
The average time to do all this, in our tests, can range from 15 minutes to 30 minutes or more. This is because part 3, where you set application permissions, is not a typical installation method. There is no need for these steps when installing either Mspy or FlexiSPY on a rooted or unrooted device so even though Webwatcher tries to help you as best it can there is quite a lot of user involvement needed too.
If you thought that installing the software on to non-rooted device would be quicker than rooted, then unfortunately Webwatcher may just prove you wrong.
All in all, once that has been done the application starts capturing data automatically and this is uploaded to the online portal.
Inside the online portal you get the following data captured:
- Installed applications
- Call logs
- GPS location
- Images
- SMS messages
- Websites visited
- Website searches
- Instagram photos
- Whatsapp messages
Please note that the Tinder option, shown in the screenshot below from the online portal, is for iPhone only and was not functional at the time of writing this report.
We will now go through each of Webwatcher’s features to show whether or not they actually work and the data that each feature actually captures.
Running Apps
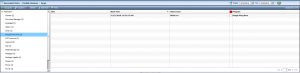
For this feature every running application is listed according to the application name.
Clicking it shows the date and time the application was ran as well as the total time that it was used.
Call logs
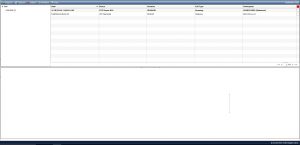
Captured and received call logs are captured along with the call duration, date and time of the calls and the number of the calls.
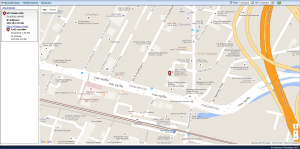
Geolocate (GPS)
GPS data was captured without any issues. What is interesting is that WebWatcher still use the Google Maps API. Many other spy phone software companies have been forced to no longer use the Google Maps API due to costs and Google’s terms and conditions for using the Google Maps API.
The location data is lacking in detail with WebWatcher only plotting the device on a map, it does not also display the actual location co-ordinates as well. That means that those who want more detailed information about where the device currently is then they cannot get this information with Webwatcher and instead must perform their own internet research.
Images
Images taken using the standard camera application were not captured. However, when using Instagram, those same images that were taken using the camera and then uploaded to an Instagram account (the Instagram application on the Play Store) were captured and uploaded.
It shows the image itself, the date and time the image was taken and the filename. It also lists the type of Image as well but in testing we only had one type of image uploaded and that was from the Instagram app
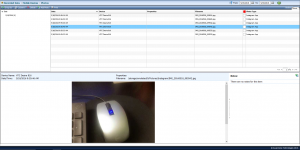
SMS Messages
SMS messages sent and received were captured without issue. Included in the captured information is the contents of the SMS message, the sender phone number, the recipient phone number and the date and time the SMS was sent or received.
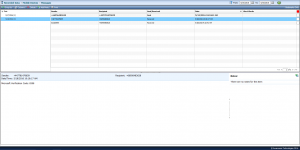
Websites Visited
The websites visited are only captured if the Chrome browser is used. It shows the date and time the website was accessed, the window title and the total time spent browsing the site. When you click a record only the visited URL is shown, there is no captured screenshot of the page or anything like that.
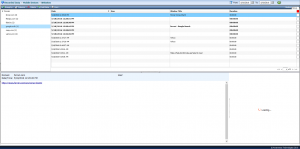
Instagram photos
As long as you have the Instagram app installed from the Play Store images taken using the standard camera application and uploaded to an Instagram account will be captured.
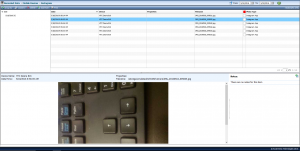
Whatsapp capturing
A new feature that WebWatcher have added for Android recently is the ability to capture Whatsapp messages without rooting the Android device. Whilst this does work and it does sound good there are a few limitations. Namely that it only captures one side of the conversation which is the side of the device with Webwatcher installed and this data is just plain text and unformatted.
That means that chat elements such as stickers, images, videos, etc. are missed. These can be just as important to a Whatsapp chat then the text itself. Otherwise, Webwatcher uploads the plain text of one side of the conversation with no issue.
For this feature Webwatcher actually deserve credit. The majority of other spy phone companies only offer IM capturing on rooted devices and then only if the IM service (e.g. Facebook, Whatsapp etc.) is a supported version. Whilst it only captures the one side of the conversation (the messages that are sent from the device with Webwatcher installed on it) this is still actually better than nothing for those who want to capture Whatsapp but do not want to spend time messing around rooting the device first.
Investigating where the scam originated from
Technically, Webwatcher is not a scam. They do actually sell real software, as we have shown here. The thing that is not so apparent though is that not all the claims that are on the website are guaranteed by the software.
For example, Webwatcher advertises itself as discrete and tamper proof. This is not entirely true. On an unrooted Android device every application is listed inside Application Manager (Apps > Settings > Application Manager) and all that Webwatcher have done is give the software a non-discrete name that it hopes that people will ignore when looking through their list of installed applications.
Furthermore, Webwatcher installs itself as a device administrator. What this does is stop Webwatcher from being uninstalled using the typical Application Manager menu. They see this as a way to make Webwatcher tamper-proof but, what they do not think about it, is how the device owner will think to find an application that they don’t seem to be able to uninstall.
Typically, in this case, the device owner will start to panic and get suspicious (because why would there be an application on there that cannot be removed? What is it?) and they will clearly research the name of the application and find out that it is Webwatcher. Because they cannot uninstall it they will just factory restore the device and that is the end of Webwatcher. No spy phone software can ever survive a factory reset.
Let’s see this in action.
Here you can see Webwatcher in the Application Manager menu.
Notice that it is not called Webwatcher.
Instead, it looks like the name of a standard Android system process. Webwatcher are hoping that this is what people will think it is and ignore it. After all, you can only remove software listed in the Application Manager menu on a rooted device and Webwatcher does not offer any root only features for their Android product.
Here you can see Webwatcher listed in the Application Manager menu. We know it is Webwatcher because it is made referred to by a device administrator installed called ‘ATI Client’ which is what we installed in part 4 of the Webwatcher installation process.
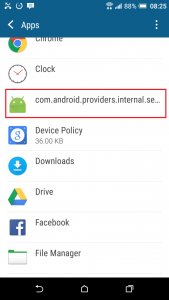
When you tap the application above, as mentioned, you cannot uninstall it. The option to do so is greyed out. This will immediately cause alarm and suspicion to the device owner.
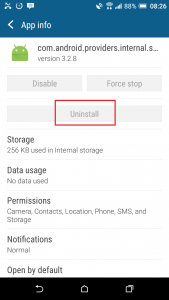
So, if we were the device owner we would be really suspicious right now and edging towards a factory reset.
However, you can uninstall Webwatcher by turning off the device administrator from the Security menu.
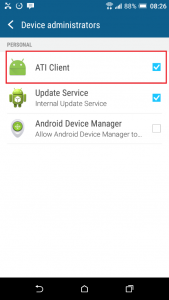
Above we can see a device administrator installed called ATI Client. This name matches what was installed by Webwatcher. We need to tap this option and then deactivate it.
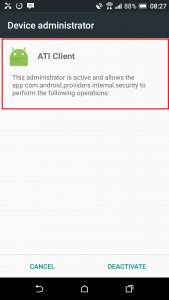
You can see in the description above that the ATI Client administrator makes reference to the same application that is Webwatcher and this is how we know that they are the same thing. With ATI Client deactivated we should be able to uninstall Webwatcher but it still was not that easy.
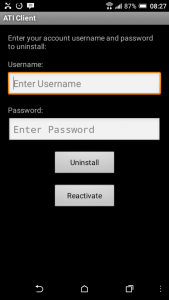
Immediately after disabling the Webwatcher device administrator Webwatcher appeared on the phone. And it doesn’t go away. If you try to leave the screen Webwatcher will just pop back up again. This will really make the device owner suspicious. The only way to get around this is to restart the device but then, after you do that, at least with us, our device would just random restart itself and pretty much become unusable.
Investigating the company
Webwatcher is a legitimate company selling monitoring software for both smartphones and computers. However, Webwatcher is created by Awareness Technologies who are based in Connecticut in the USA. Awareness Technologies also make the same Webwatcher program under different names such as Laptop Cop, Interguard and SONAR.
Their website is easy to find and heavily advertises Interguard as their main product. Webwatcher is simply the smartphone module of Interguard refactored in to a different and easier to use product.
Suffice to say, this is not something new. The majority of these companies (Mspy, Mobile Spy etc.) often peddle the same product with a different name and a different look in order to appeal to more clients. This also means that customers can easily be fooled in to believing that a new product that sounds better than their current one is actually the same thing. This is scam tactics which makes Webwatcher part of a scam too, even if you do get working software.
Protecting yourself from scams like this
We want to buy back your license from these scam vendors and you can then purchase a FlexiSPY license at a discounted rate.
Spy Phone Review is here to help!
Simply head over to FlexiSPY’s buy back page which is located here to get started.